2.2 Blocks: The Building Units of the Chain
Blockchain gets its name from the way it structures data: blocks of information chained together, each containing a set of transactions and a reference to the block before it. This creates a continuous, chronological chain of information that’s stored across many computers. Once a block is added to the chain, it’s extremely difficult to alter, making the blockchain secure and trustworthy. When one block is full (or after a certain time interval), a new block is created to record subsequent transactions.
Inside a Block
Each block contains several key pieces of information: a list of the recent transactions, a timestamp, and a special code called a cryptographic hash of the previous block. This hash is like a digital fingerprint: it is produced by running the block’s data (and some other block headers) through a cryptographic hash function. The output is a fixed-length string of letters and numbers that uniquely represents that block’s contents. Even a tiny change in the block’s data–say, altering one transaction–would produce a completely different hash. By including the previous block’s hash in each new block, the blocks become linked in sequence.
For example, imagine writing one page of a journal and then copying its unique ID on the next page. If someone later tries to change Page 1 without updating Page 2’s reference, the IDs won’t match. Similarly, each blockchain block “points back” to the prior block via the hash, forming a chronological chain. The very first block, called the genesis block, has no previous block, but all others form a continuous chain back to it.
This chained structure is fundamental for integrity. Because every block contains the hash of the one before it, the data in any block cannot be changed without altering all later blocks in the chain. In practice, this makes the record tamper-evident. Anyone trying to rewrite history would have to re-compute the hashes of the changed block and all blocks after it–a monumental task if many blocks have been added since.
Key Components of a Blockchain
Cryptographic Principles
Cryptography is the science of securing information, and it’s the cornerstone of cryptocurrency security. In cryptocurrencies, two key cryptographic tools are used: public/private key pairs for authorizing transactions (which we’ll explore in module 5) and hashing for securing data. These ensure that only authorized users can spend their funds and that the blockchain remains tamper-proof.
Hashing: The Cryptographic Glue
The cryptographic hash function is the “glue” that holds the chain together. A hash function is a one-way mathematical operation that takes any input (even a large block of data) and produces a fixed-length output (e.g. a 64-character string).
It has two important properties:
(1) It is deterministic (the same input always produces the same hash)
(2) It is practically impossible to invert or predict (you can’t guess the input given only the hash)
These properties mean the hash acts like a fingerprint or digital seal. If the block’s content changes, even slightly, the resulting hash changes drastically.
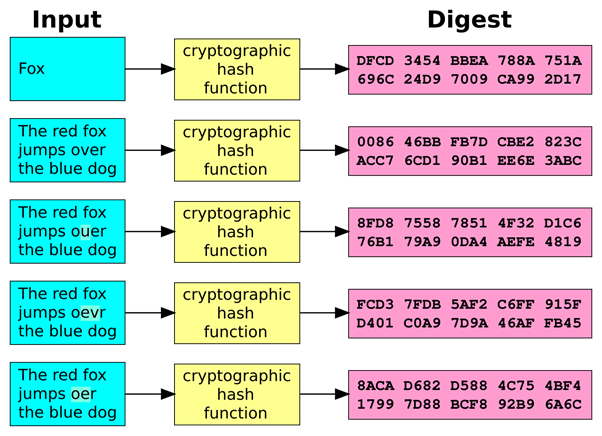
In blockchain, after a block is filled with transactions, its contents are run through the hash function to generate the block’s header hash. This hash value is then stored in the next block’s header, along with that block’s data. By continuously chaining these hashes, any change is immediately apparent: the altered block’s new hash won’t match the one recorded in the following block.
Try a Blockchain Hash Function (SHA-256)
This demo allows you to type in any text and see its SHA-256 hash, which is a unique code created using the browser’s built-in Web Crypto tool. If you make even the slightest change to the text, the hash will look completely different. This shows how sensitive the hash function is, which is a key feature that helps keep blockchains secure.
Now that you understand how blocks function as the fundamental units of a blockchain—each securely storing data and linking to the next—it’s time to explore how the system stays secure, accurate, and tamper-proof. In the next lesson, Nodes, Consensus, and Mining: Keeping the Chain Honest, we’ll examine the roles of network participants, how decisions are made collectively, and how new blocks are verified and added without a central authority. This is where the true power of decentralization comes to life.

